We analyzed data breaches and cyber-attacks of 2018, here are the key insights

Earlier this year we launched Breachroom, a free service that collects and classifies cyber-attacks and data breaches that are occurring globally. For the year 2018 we ended up recording more than 70 breaches across a variety of industries and geographic regions. Analyzing this data set, now that the year has come to a close, shows that it was an exceptionally bad year with lots of high profile data breaches. Companies such as Under Armour, FedEx, Adidas, British Airways, T-Mobile, Facebook and Marriott all faced severe data breaches. Some companies are still down in the trenches battling with the aftermath of their cyber security incident, renewing their focus on improvements to their defense and upgrading policies.
 Breachroom map view
Breachroom map view
Roughly half way through the year I noticed that smaller tech companies are starting to focus on security and making investments that improve their companies security posture. This was in part motivated by data breach headlines and the GDPR panic, but also triggered by a rise in sensitivity about data protection, which reflects in today’s enterprise sales process. Filling out security questionnaires before closing a deal is quickly becoming standard practice, especially with tech companies handling data.
The 2018 Templarbit Breachroom data set
Let’s dive into the 2018 Breachroom data and get a better understanding of the challenges companies faced in the previous year and how things might improve in 2019.
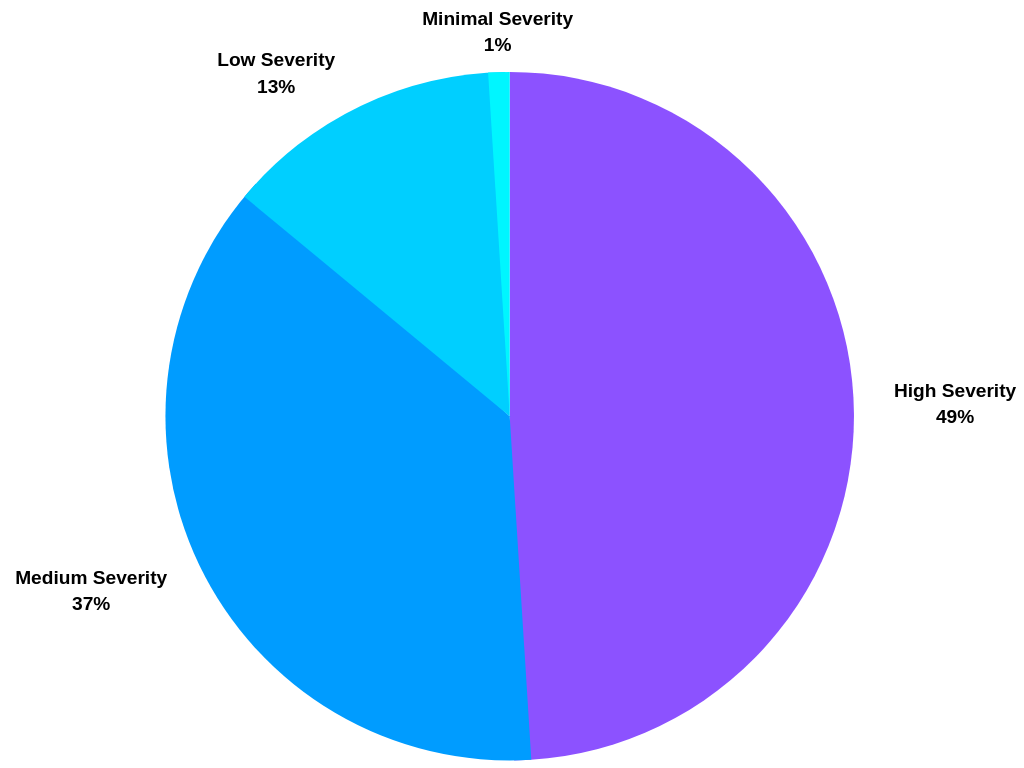
Severity Distribution
Breachroom labels each cyber-attack with a severity score. This score gets set by one of our cyber threat analysts based on publicly available data such as the scope, exposed information and business impact. In 2018 we have not seen an attack with the highest severity level 5, but almost half of all breaches got classified as very severe (level 4).
Severity distribution
The combination of a growing mountain of personal data flowing through large portfolios of software services and hackers augmenting their abilities with new tooling have made for a situation that currently favors the bad guys. What is particularly interesting is the growing number of AI/ML hacking tools that allow one soldier to take on many potential targets, knocking on doors until one is found that isn’t sufficiently secured.
Target Company Locations
A unproportionally high number of successful attacks targeted American companies, with a special focus on California. In fact, 1/5th of all breaches happened within the golden state, with an especially high density around San Francisco and Silicon Valley. Overall nearly 70% of breaches occurred with U.S. companies, followed by targets in the UK and Japan.
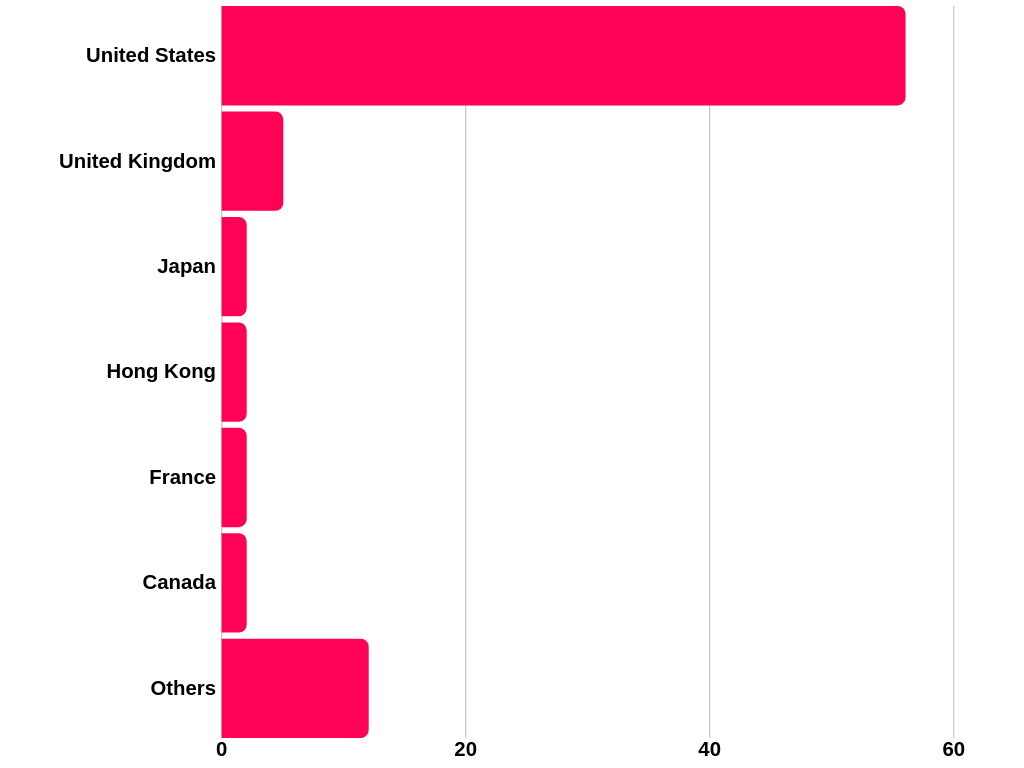
Attack Locations
Attack Vectors
Researching the attack vector for each breach was challenging and many times we had to fall back to a generic label that simply declared the incident as a Data Breach. But what did surface in the data was the problematic situation in AppSec. Nearly half of all attacks came through the application layer, mimicking the sentiment of other annual data breach reports. For example the Verizon Data Breach Investigations Report also shows that the Application Layer is the number one attack vector.
The problem with application layer security is one that sits much deeper than patching vulnerable dependencies. Ensuring secure and healthy web applications and APIs in a world of rapid deploy cycles is a big challenge. Solutions to help with this problem are evolving and security as a whole is moving much closer to the application, something we actively help shape at Templarbit.
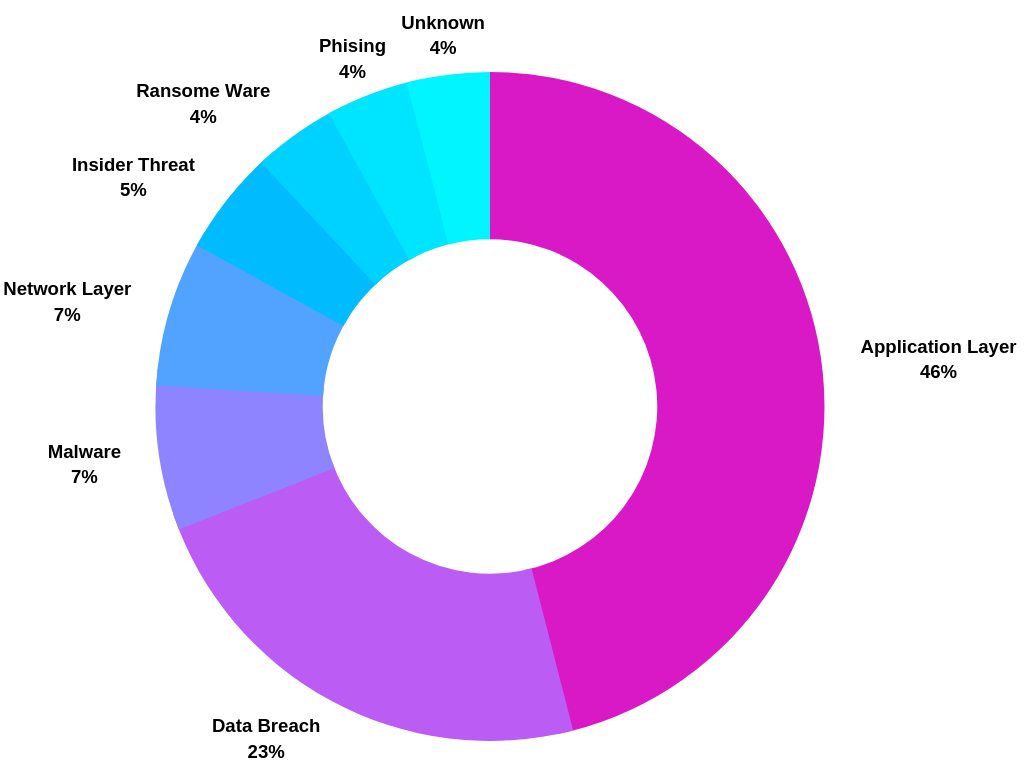
Attack Vectors
2018 also saw a rising trend in data leaks and exposures. Specifically data with a lack of proper protection was often found to be just floating around online without even the most basic security such as a password needed to access it. Fully exposed databases and PII data was easily found, yet could have been entirely preventable.
Communication Strategies
A clear split can be observed between companies in how they decided to address communication of the security incidents. While 49% of companies decided to disclose the breach right away, a slight majority decided to leave the public in the dark for much longer. In some cases more than 9 months had passed before the incident was made public. About 100 days seems to be the average time from initial discovery of a breach to publicly disclosing the event.
Both the media and customers have the expectation to know about a breach as soon as it is discovered. The longer the delay in communicating a breach the greater the reputational damage a company faced. A sweet spot seems to exist in where a company takes its time to perform an initial investigation so that the incident can be properly communicated to the public. A good example that was positively received was the clear and transparent report published by reddit, two months after being breached.
What’s ahead
Predictions are hard but if I was forced to give one I would say that in 2019 we will see even more data leaks and exposures. Many of them will be due to problems in the application layer, phishing and unprotected lakes of data floating around the public internet.
At the end of 2019 California’s consumer privacy law is set to go into effect and I believe that this will bring us a mild déjà vu of the GDPR panic from 2018. It will focus even more startups and SMBs to start directing some of their efforts to improving how they are handling data. We will also see more companies consider investing in monitoring solutions and security policies.
As serverless architecture is seeing wider adoption we will probably see an increase in breaches that originate in that part of the stack. They easily allow devops teams to run stateless functions on demand, increasing the footprint of software that has access to sensitive resources. Companies investing in AWS Lambda, Azure Functions or Google Cloud Functions should also invest into increasing their visibility into their application layer.
Templarbit will continue to track security incidents and compile them on the Breachroom. If you are now wondering where your company’s security posture can be improved or simply would like to learn more about us and our products you can schedule a meeting here
