The story of why Chrome and Firefox will soon block sites with certain SSL certificates
In the near future, Google Chrome and Mozilla Firefox will begin distrusting SSL certificates from Symantec, GeoTrust, Thawte, VeriSign, Equifax, and RapidSSL. This change will take effect when Chrome 70 beta and Firefox 63 beta are released in early September. The stable public release of Chrome 70 and Firefox 63 is slated for October.
There is a long history between Google and Symantec that has led to this decision. Back in September 2015, Google’s Certificate Transparency project flagged a few Google domain certificates that were improperly issued by Symantec’s Thawte, a root certificate authority. These certificates were neither requested nor authorized by Google. Symantec immediately revoked them upon realizing that they were inappropriately issued and announced the certificates were accidentally released to the public during an internal product testing procedure. Initially, Symantec reported the issue was only contained to three domains. However, an official incident report from Symantec was released a month later to the public stating the number of improperly issued certificates was contained to 23 certificates across five organizations instead. Within a few days, Google rebutted the official Symantec report. Symantec reopened their investigation and reported that instead of 23 certificates it was 187 improperly issued certificates across 76 organizations and 2,458 certificates for nonexistent domains.
Google’s next official statement included a list of demands for Symantec. Symantec was to undergo a third-party security audit and a Point-in-time Readiness Assessment, an assessment to access whether or not Symantec is complying with several Certificate Authorities principles and criterias. All certificates issued by Symantec after June 1, 2016, are to support Google’s Certificate Transparency project. Symantec was also told to update the public incident report with more details and provide steps they plan on taking on to prevent something like September 2015’s incident from happening again. It seemed that was the end for the Symantec mis-issuing fiasco.
A couple years later in January 2017, a security researcher, Andrew Ayer, discovered that Symantec-owned certificate authorities issued more invalid certificates. Google launched their own investigation and concluded something even worse: the 2015 mis-issued certificates incident was not an isolated event. The number of mis-issued certificates over the span of a couple years was at least 30,000 and Symantec had allowed at least four outside parties access to their infrastructure. Many of the invalid certificates that Andrew Ayer found contained the word test in the domain name or had obviously fake values in the subject distinguished names like an organization named “test” in test, Korea. Google then released the official proposal to distrust Symantec certificates because of Symantec’s unwillingness to change their ways for the safety and security of their customers and the public.
“On the basis of the details publicly provided by Symantec, we do not believe that they have properly upheld these principles, and as such, have created significant risk for Google Chrome users. Symantec allowed at least four parties access to their infrastructure in a way to cause certificate issuance, did not sufficiently oversee these capabilities as required and expected, and when presented with evidence of these organizations’ failure to abide to the appropriate standard of care, failed to disclose such information in a timely manner or to identify the significance of the issues reported to them.” -Ryan Sleevi
In March of 2018, Google released their official timeline to distrust all Symantec and Symantec-owned certificate authorities (GeoTrust, Thawte, VeriSign, Equifax, and RapidSSL). A couple days later, Mozilla releases their official announcement that they will match Google Chrome’s timeline to distrust Symantec certificates.
Google and Mozilla’s distrust of Symantec and sub-brand certificates (GeoTrust, Thawte, VeriSign, Equifax, and RapidSSL) means your users will see a warning page blocking the path to your website when they are using Chrome and Firefox. The best way to clear the path to your site is to acquire a new certificate that isn’t from Symantec or its subsidiaries. The warning page will remain on your site path until a new certificate is acquired.
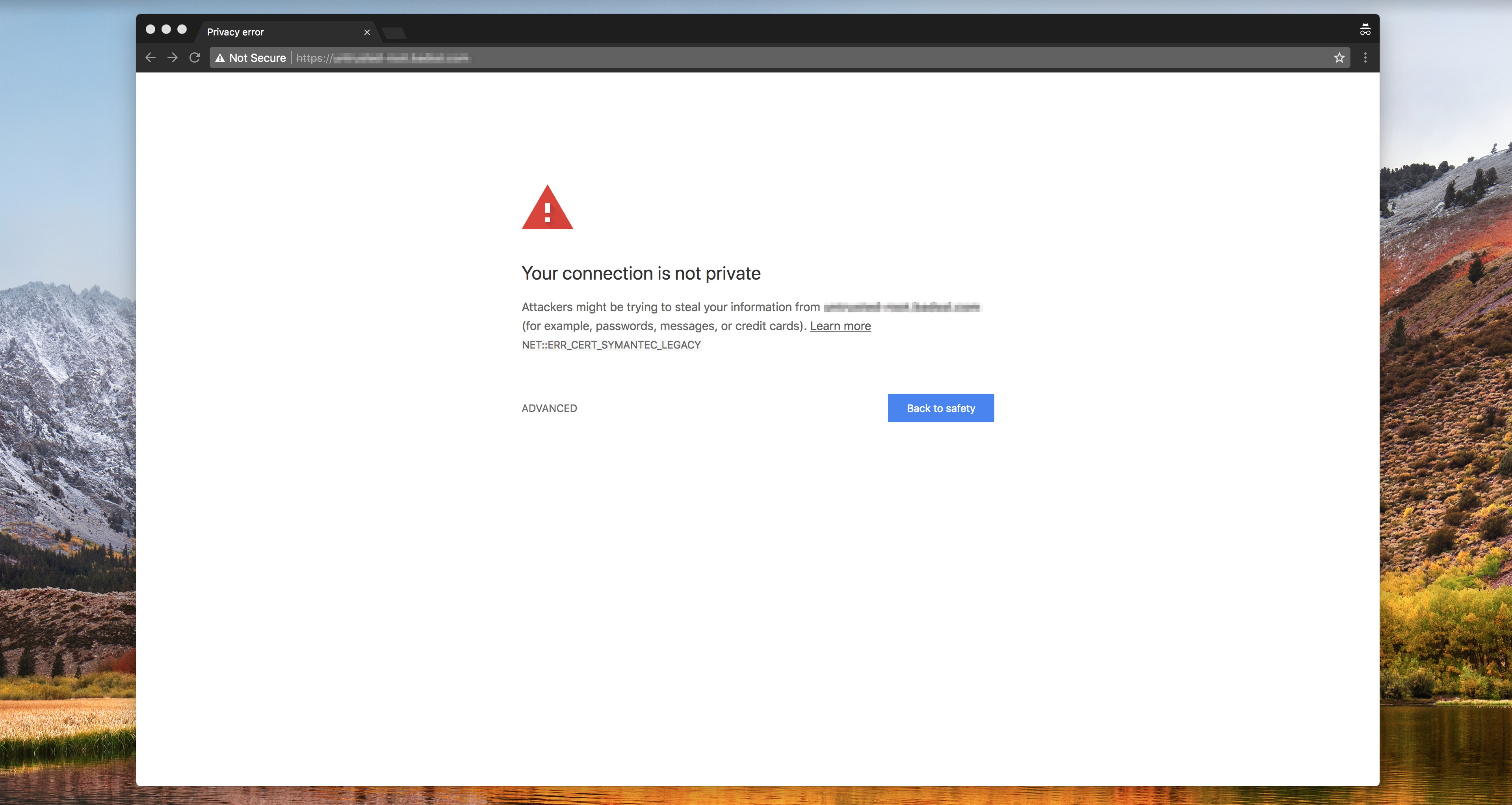 Google Chrome 70’s warning page
Google Chrome 70’s warning page
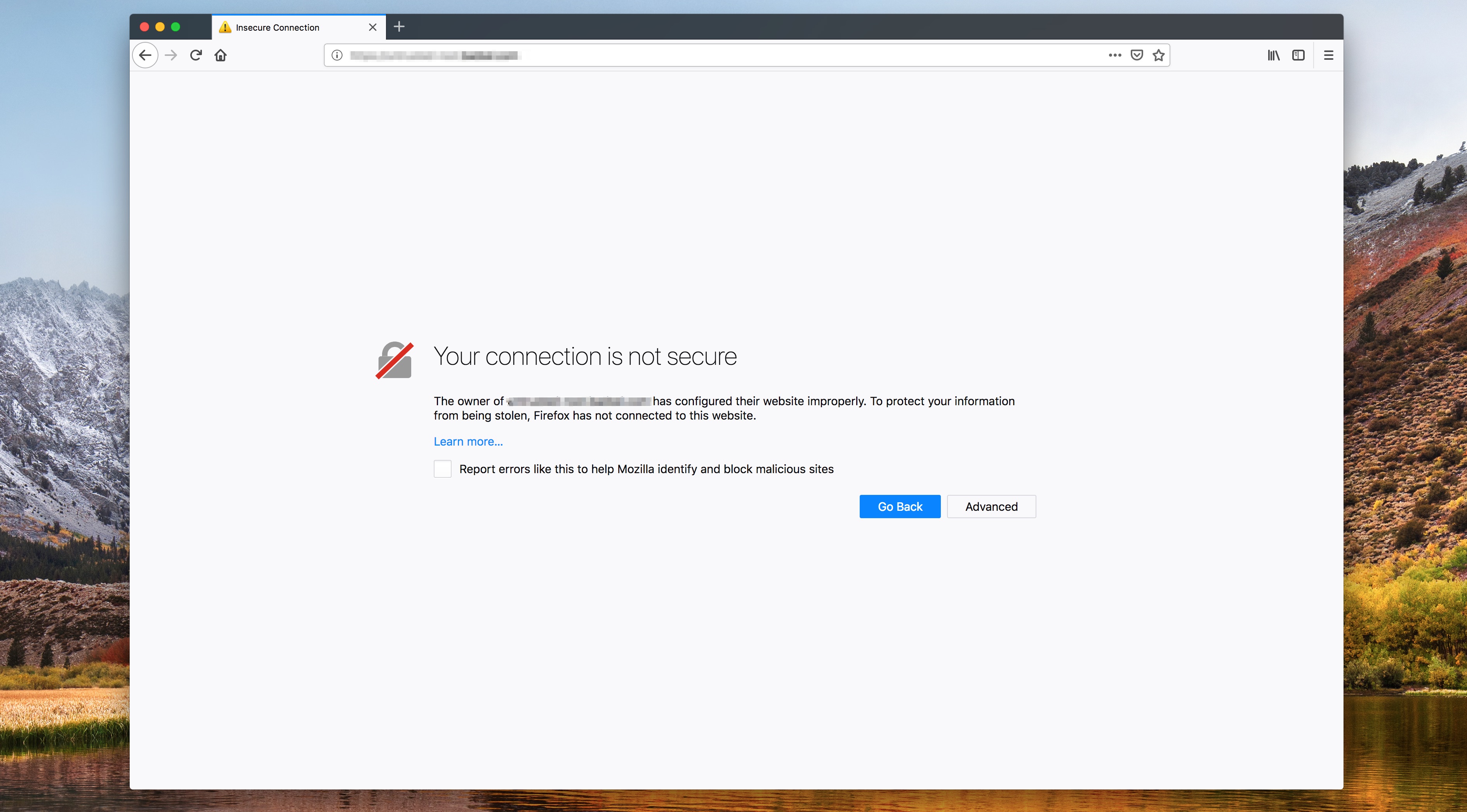 Mozilla Firefox 63’s warning page
Mozilla Firefox 63’s warning page
If you are now wondering if any of your sites or web applications are using SSL certificates that Chrome and Firefox will soon block, you can use the Templarbit Security Check to find out if you are still using any of the Symantec certs.
