Highlights of the Verizon 2018 Data Breach Investigations Report
Verizon just published the 11th edition of its Data Breach Investigations Report. The report is comprised of real-world data breaches and security incidents and provides both companies and security experts with some of the most interesting data around the state of cyber security. This year the team has analyzed 53,000 incidents and 2,216 confirmed data breaches. Here are some of the highlights.
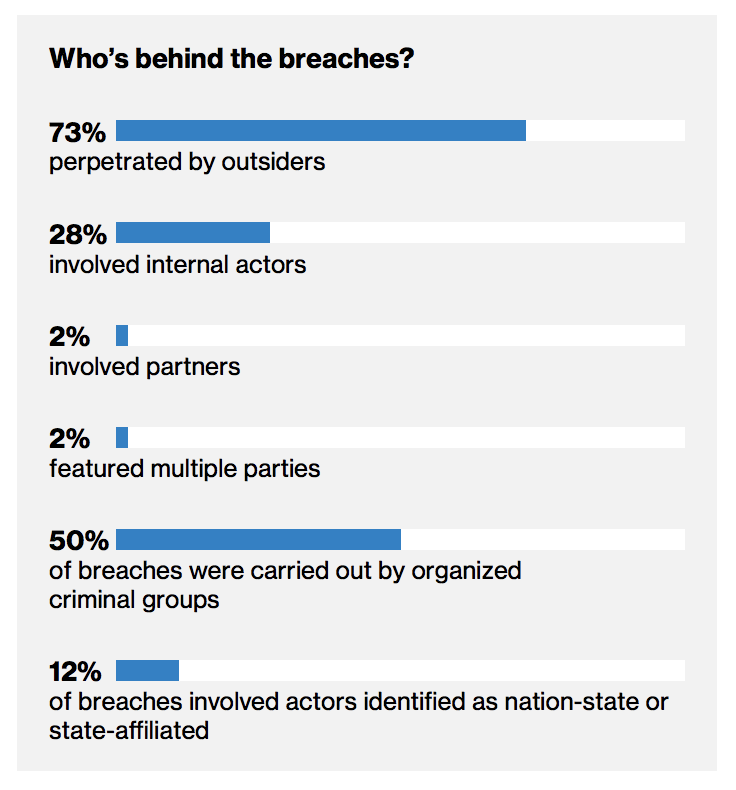
Who’s behind the breaches?
Most of the data breaches are caused by outsiders but surprisingly almost a third of them involved internal actors. Organized criminal groups caused a stunning 50% of the breaches where as nation-state sponsored activity is lower in volume.
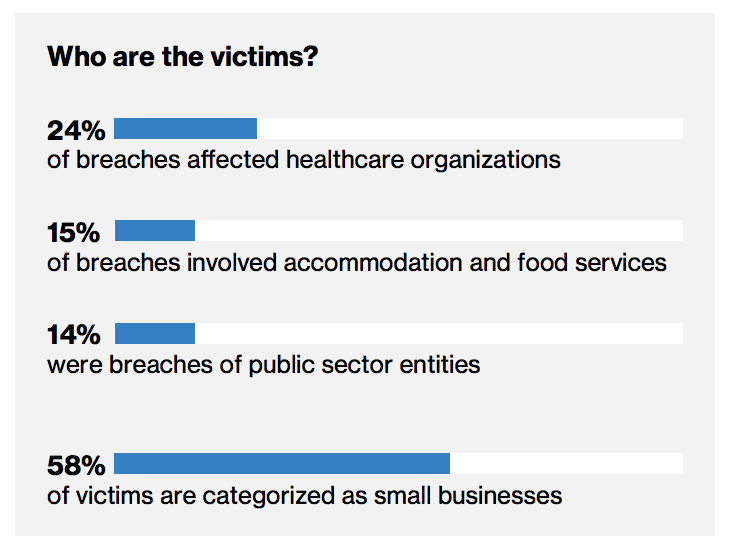
Who are the victims of these breaches?
58% of victims are categorized as small businesses. This isn’t a huge surprise, since SMBs are both the largest group and the ones most resource constrained in their security efforts. The healthcare industry continues to be of particular interest to hackers, the sensitivity of the data and it’s value on deep web marketplaces make them a prime target.
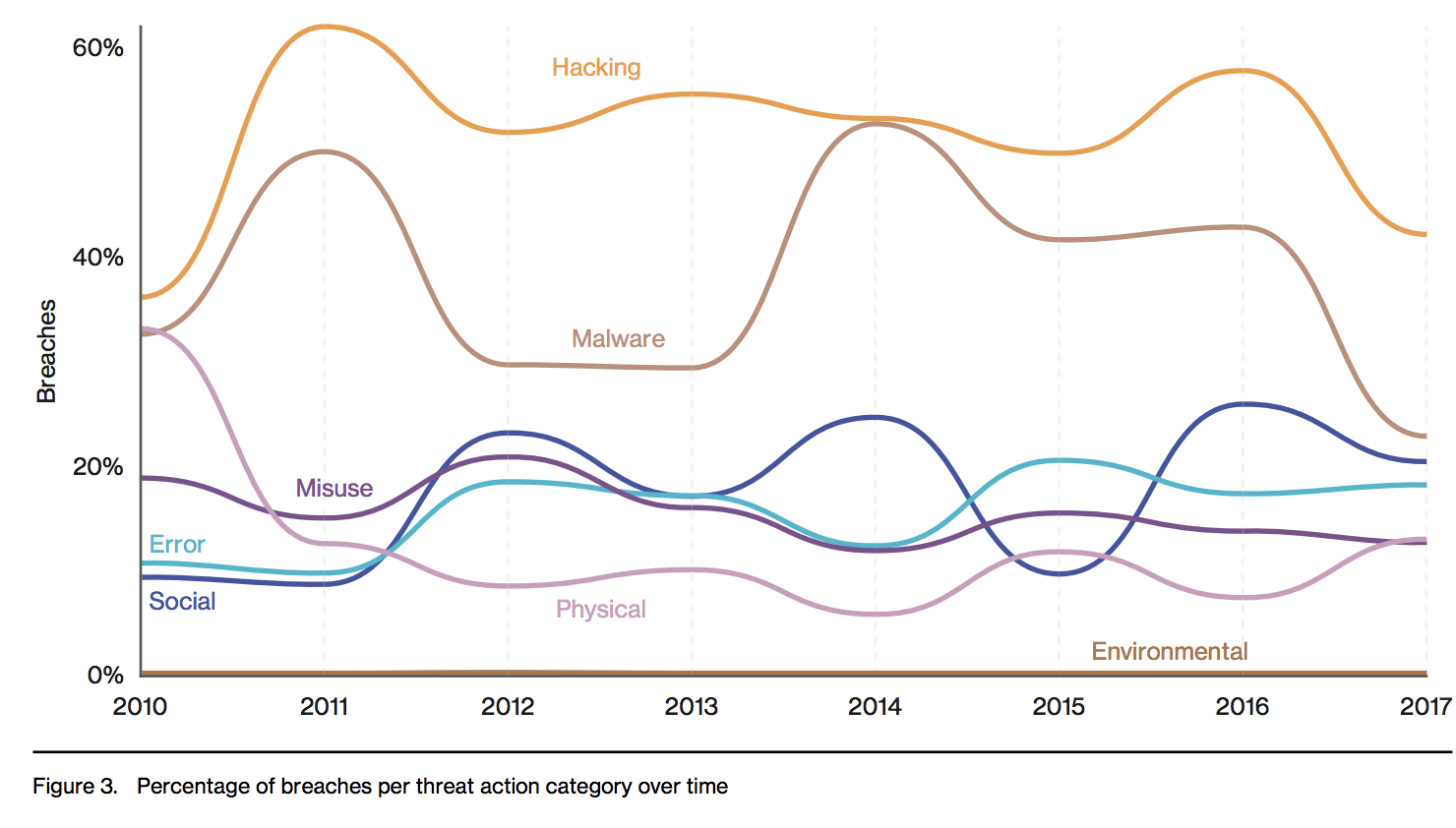
What tactics are utilized?
Actor motives have historically been driven by financial gain, followed by espionage. Just under 90% of breaches fall into these two motives, with money again leading the charge here. Hacking and Malware are still the two most utilized tactics used in data breaches. Malware and hacking often goes hand in hand when breaching is a target. A common path to the use of stolen credentials is installing malware capable of keylogging a victim. Botnet and ransomware are both flavors of malware that you should invest in the operational ability to find and remove these types of malware from your systems.
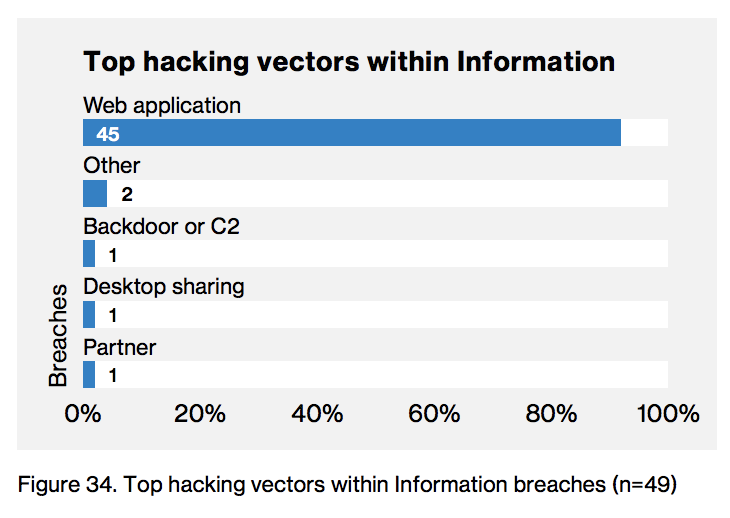
The top attack vector continues to be Web Applications
Web Application Attacks make up the majority of breaches in the report. The three most common hacking techniques used are account takeover, code injections, and path traversal attacks. This affects all verticals from retail to the public sector, but especially finance and tech companies. E-commerce applications are an especially critical asset. Defenses against availability as well as integrity and confidentiality losses must be implemented, tested, and refined.
What can you do in 2018 to increase your security posture?
Increase your AppSec
When breaches are successful, the time to compromise continues to be very short. Increasing your ability to monitor for malicious activity especially inside your software applications is a meaningful change you can implement. Attackers also often walk the easy path by exploiting known vulnerabilities in popular dependencies. Applications and APIs using components with known vulnerabilities undermine application defenses and enable various attacks. Remove or upgrade those components and always be monitoring.
2FA everywhere
Implement two-factor or multi-factor authentication in your enterprise for those who administer any web applications or databases. If at all possible establish two-factor authentication with all users in your organization.
Security check yourself
Routinely implement and execute a checklist for general security hygiene, and have system administrators make sure that the systems you build are built to deploy patches and updates in a timely fashion. Automate anything you can as this reduces the human error associated with many breaches we see. Conduct routine scans to discover misconfigurations before an adversary does.
You can also use our free security check tool to quickly get started on your checklist
Separate sensitive data
It is a good strategy to keep highly sensitive data separated from the rest of your network. A data vault with access restricted to only those individuals who absolutely require it. Monitor that access routinely to make sure the data is not being copied, moved, or accessed in a suspicious manner.
Within the 53,000+ incidents and 2,200-odd breaches you’ll find real takeaways on what not to do, or at the very least, what to watch for. I encourage you to read the full report, available as a free download here:
https://www.verizonenterprise.com/verizon-insights-lab/dbir/
I also encourage you to take a look at Breachroom where we keep a current list of data breach information.
Templarbit is working to build more robust solutions that address global enterprises’ AppSec concerns. We’d love to hear what you’re working on, what keeps you up at night, and see how we can tackle these challenges together. You can reach us via email at our contact form
